Something about commercial VPN Services : My concerns

In the previous article, I’ve exposed here the concept of a VPN, what’s happening when you using one, and what do the commercial services are offering. Now, I’ll explain why I don’t trust them, and why I won’t use them.
And by extension, why I will never write any “sponsored content” for them.
Once again, that’s just my personal opinion, do whatever you want !
Common misconceptions and misinformation
Some benefits exposed by the providers are not true or incomplete. Other are just side effects of an actual VPN operation. And some other ones are just false assertions.
A VPN does not provide anonymity or actual privacy
Yes, a VPN actually “hides your IP”. To be more specific, when using a VPN, you’re client address as seen by the called service is the VPN provider’s one. That’s a side effect of using a VPN as your Internet trafic is redirected through the VPN provider’s network. Just like at work where I’m seen being in Paris because the proxy is located there, while I’m not physically there.
But, it’s been a long time since the IP address is no longer a trusted identifier on Internet. Because all of the IPv4 ranges are attributed and there are not enough address for all of the clients, the ISP are commonly using workarounds like assigning to various clients the same IP and use a NAT/PAT for them. With IPv6 that could be different as also every device could have its own IP, but now there are for more advanced methods to profile a user.
A VPN does not make your Internet connection “private”. As I’ve said in the protocol description, a VPN establish a secured virtual direct link between two networks. So, the trafic inside the VPN is indeed private, or is expected to be if you trust the provider.
A VPN cannot protect you from your web browser
Nowadays, tracking users with their IP is simply irrelevant and useless. The web browsers are a very advanced piece of software which is almost an OS (think about Google’s Chrome OS… that’s a Linux distro using the Chrome browser as a Desktop Environment, and think about the Electron Framework). The browser is the actual attack surface for every profiling companies.
A VPN cannot protect you from tracking cookies or device fingerprinting because these actions are made before its intervention in the chain.
The device fingerprinting is a method using several components of your web browser to create the most possible unique identifier. When your browser sends a request to a site, the tracking code hosted by it will retrieve several informations to create the most possible unique fingerprint of your browser :
- User agent (containing the browser name, version, your OS)
- Screen resolution
- Location
- ISP
- Installed fonts
- Hardware setup
- And various other seems-to-be insignificant data
The device fingerprint can be completed by the “Advertising ID” which is implemented in Microsoft Windows, Android, and Apple systems. If you don’t disable it - and trust that it would be actually disabled - your operating system will be basically assigning to your device a unique ID for advertisers companies.
On the browser side, these data are stored into Cookies, especially third-party Cookies. The Cookies are small files stored in your browser put by websites containing some information for them. Typically, a legitimate usage of cookies is to keeping an active user session on a service or setting preferences. By design, Cookies can be read only by the website domain that declared them.
Example : a cookie put by https://blog.zedas.fr would be only readable while surfing on https://blog.zedas.fr.
It’s an example, if you check your cookies here you should have none, or I’ll be worried.
Third-party cookies are, and that’s why they’re called like this, put by third-party domain while visiting a website. A normal cookie is set by the website owner, a 3rd-party is set by somebody else. They are usually used for advertising and tracking, for example Google Analytics or Social Medias buttons. However they can also have a more legitimate usage, like storing user preferences across various domains of a service.
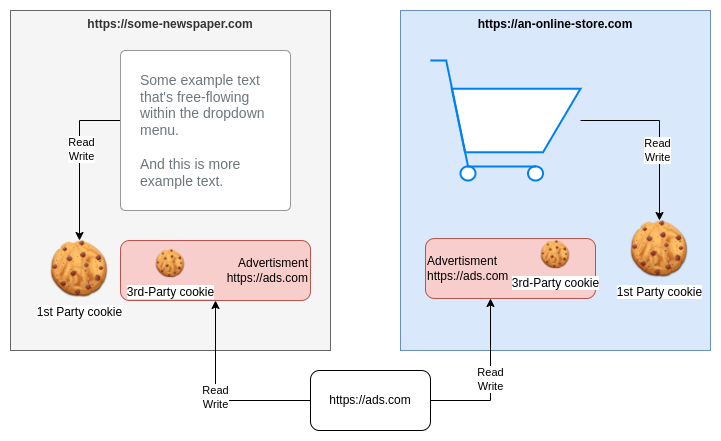
In this example, we have an Online Newspaper and a Store displaying the banners from Ads.com. Because Ads.com can store a third-party cookie for each of these website, the cookie can track and register the user activity for both of them. This is a very common way to track the user online activity across various websites.
Nowadays, cookies are generally unreadable because their content is encrypted by the server. Pretty convenient, isn’t it ?
A VPN cannot prevent cookies and fingerprinting. However, some of these services include URL or domain filtering of well-known tracking websites. But that’s also what your browser can do with a content-blocker without redirecting all of your traffic to another network.
There are possibilities to protect your browser from fingerprinting :
- Disabling the cookies (or at least the Third-party)
- Disabling Javascript
- Ensure your privacy settings are turned-on in you browser
- Using a Content blocker able to block trackers and ads
- Using a fingerprint resistant browser
- Using the “Private surf” feature of your browser
- Disable the “Advertising ID” in your OS
However, these recommendations have a cost : the user experience could be highly degraded on most websites because the majority of them are relying on Javascript. Blocking third-party cookies should be the first thing to do, but it could sometimes broke some services. I’ll propose below a series of recommendations based on the previous list.
A demonstration of tracking
On a virtual machine, I’ve setup a basic installation with my favorite web browser. Vivaldi’s ads and tracking blocker is enabled. I’ve subscribed and installed the client of a VPN Service of my choice.
I’ll do some basic tests :
- Checking my IP Address on https://www.whatismyip.com
- Going to Google searching for something
- Going to fosstodon.org and login
- Checking if while a VPN is mounted I’m seen as protected or not
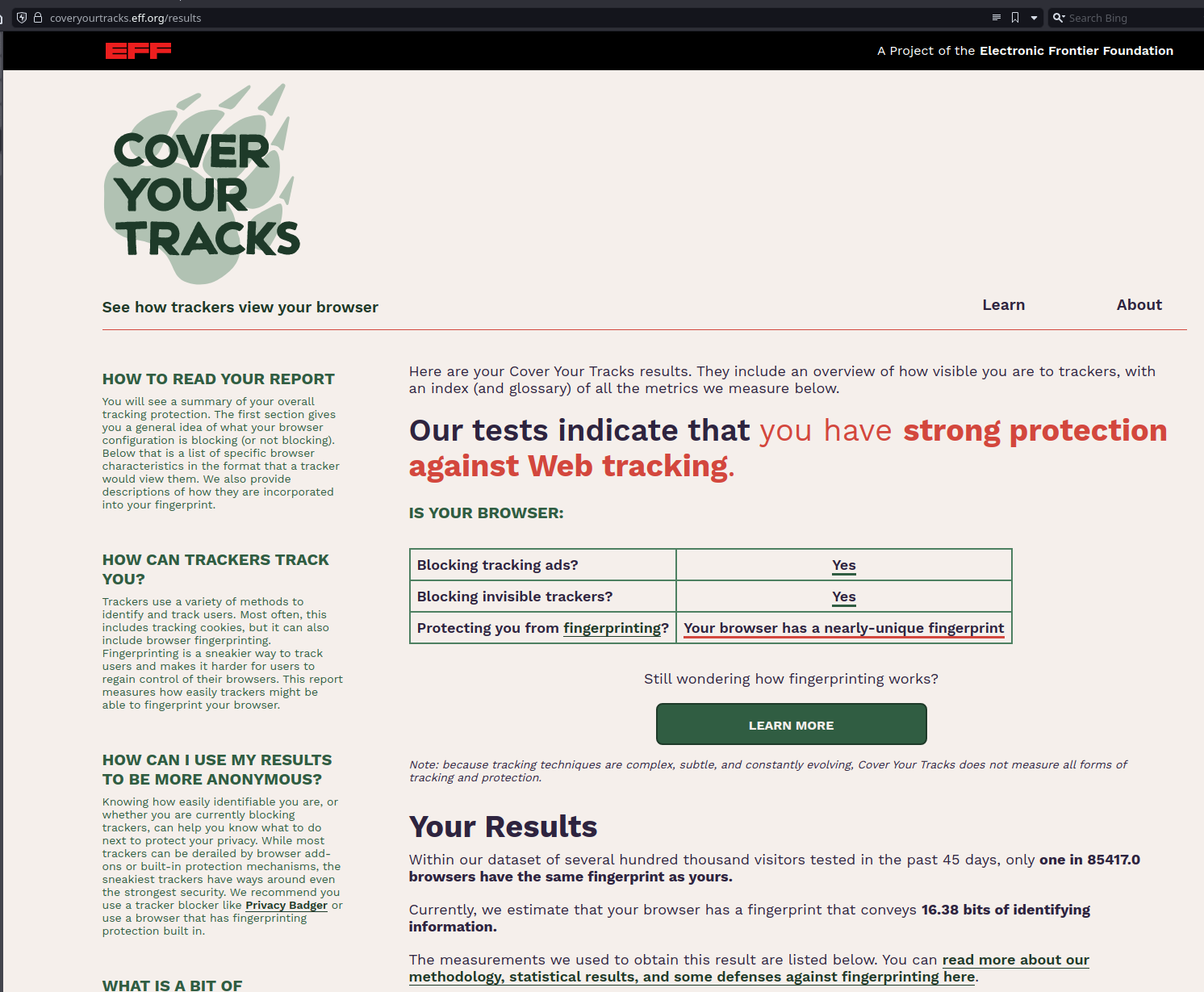
- Analyze my browser with the EFF’s Cover your tracks service to check my fingerprint
And check if mounting a VPN has any impact on the behavior of this surfing session.
Without a VPN activated
According to What is my IP, I’m indeed connected with my ISP which is Orange France. Fun fact : the City which I’ve covered is almost 900km away from my actual location. This is BTW a good demonstration for how irrelevant the IP address could be now.

Now, I’m going to google.com. As it’s the first time I’m opening this website with this browser, I have the wonderfull cookie banner asking me to consent to a colonoscopy.
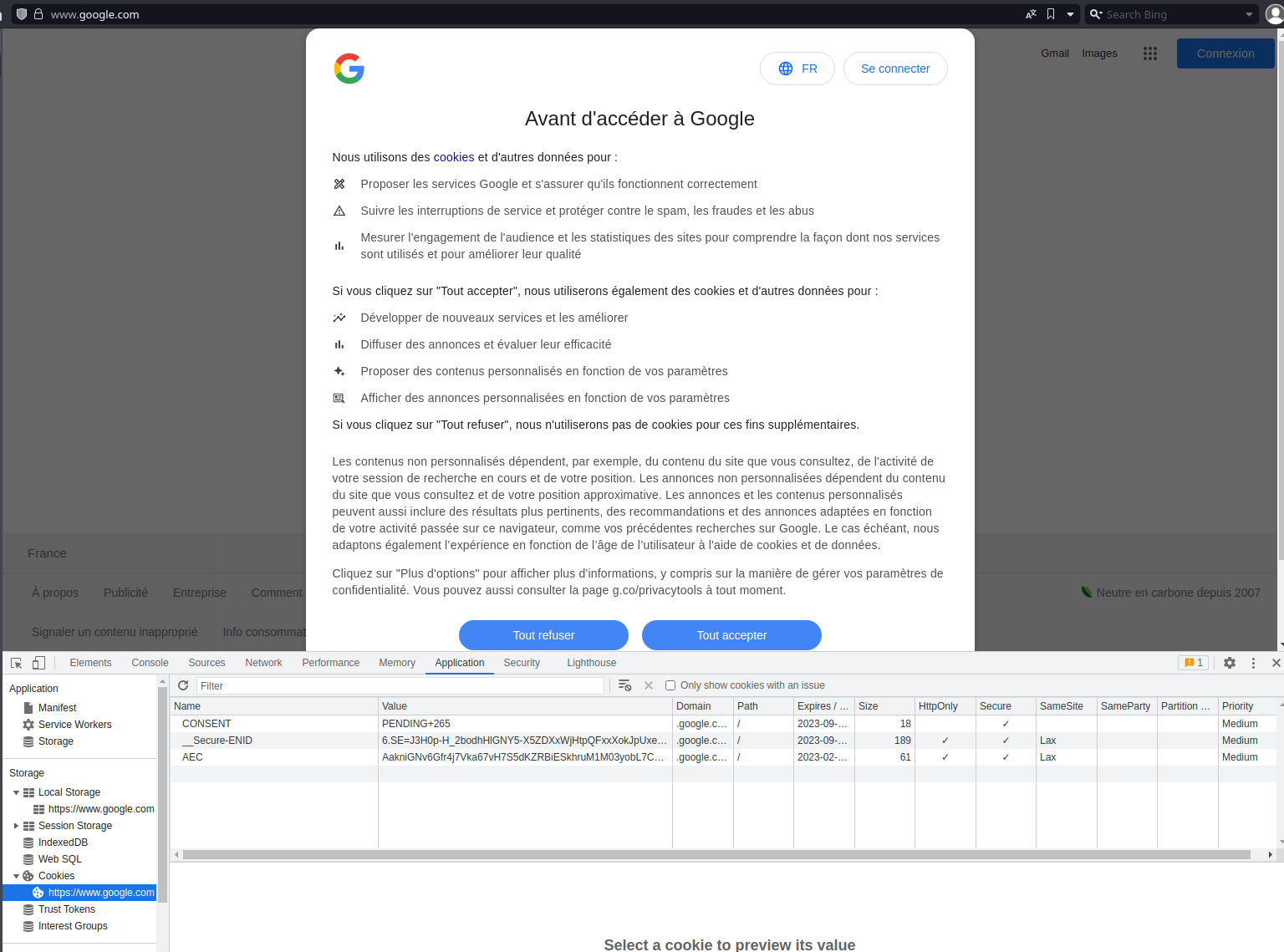
As you can see, Google has already set cookies on my browser without waiting for my consent. Also, the browser is set to display pages in English, Google is displayed in French because they adapt the language according to the detected location an not to the browser preferences. How stupid.
I’ve accepted the cookies, now I have this in my browser.
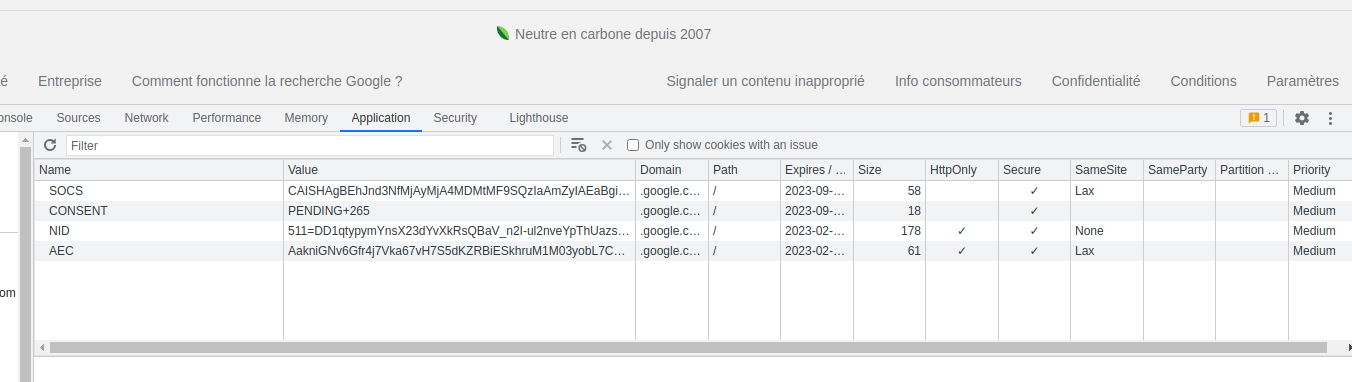
I’ve searched for “something” and get this cookies orgy in return.
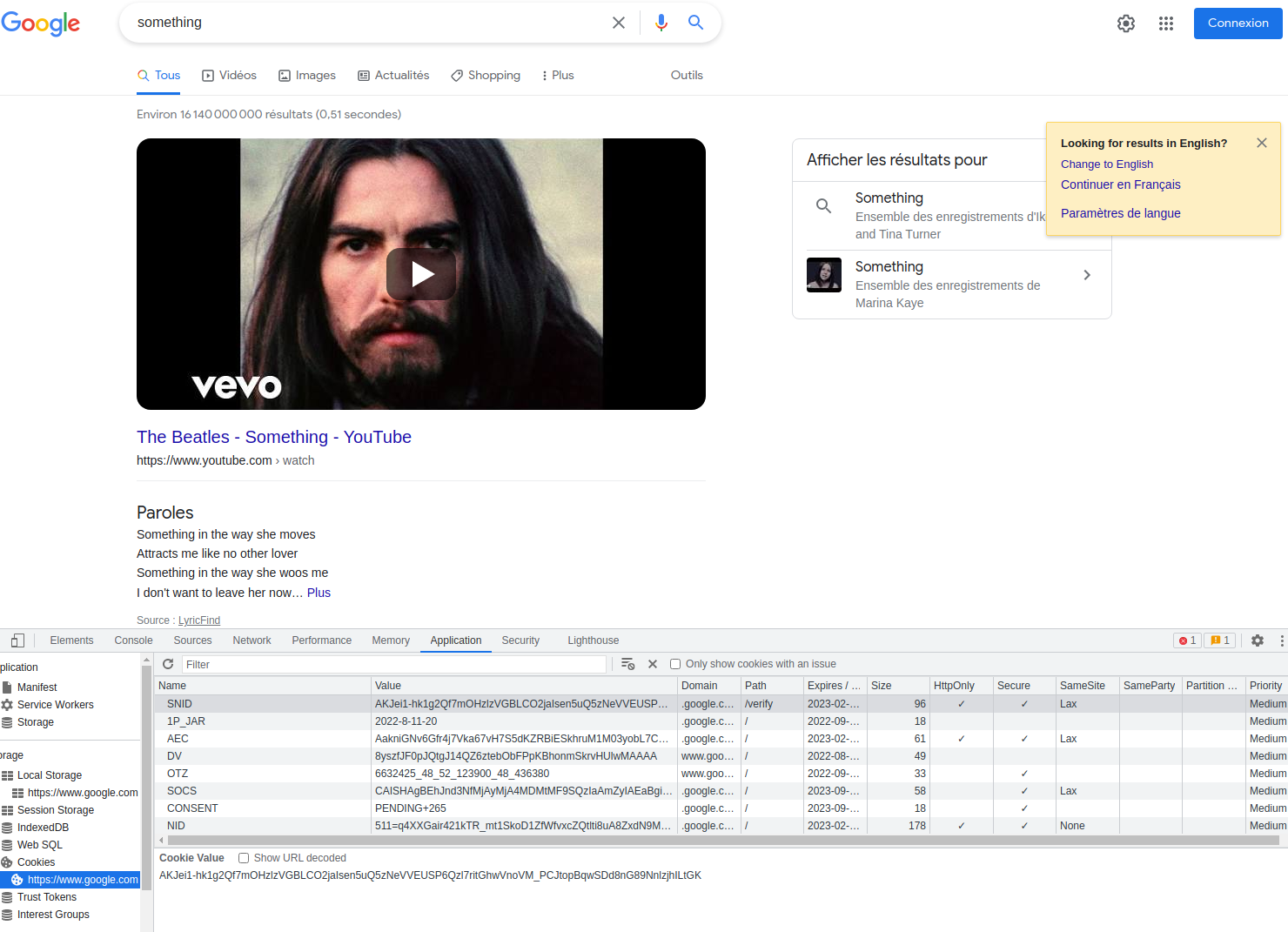
Now, let’s go to Fosstodon and login into the service.
And we’re here.
I’m going to one of the other VPN Service website to check my status, it’s confirmed, I’m unprotected.
Finally, let’s go to Cover Your Tracks to see our web tracking protection, and without a VPN I’ve already have a good one just because I have an ads and trackers blocker enabled. But my browser is still too much fingerprint-able.
With a VPN mounted
My IP changed, I’m now located in Netherlands (hello from there).

Google still knows me. And because the VPN endpoint is located in Netherlands, the GUI is translated in Dutch.
Between parenthesis, that behavior is really dumb and annoying in my opinion. That’s a good example to show how Google think they know you better than yourself. Just because of your location, they assume your language would be “this one” and not the one YOU asked in your browser. That’s stupid.
So I’ll just quote Linus’s words about Nvidia but addressed to Google. Parenthesis closed.
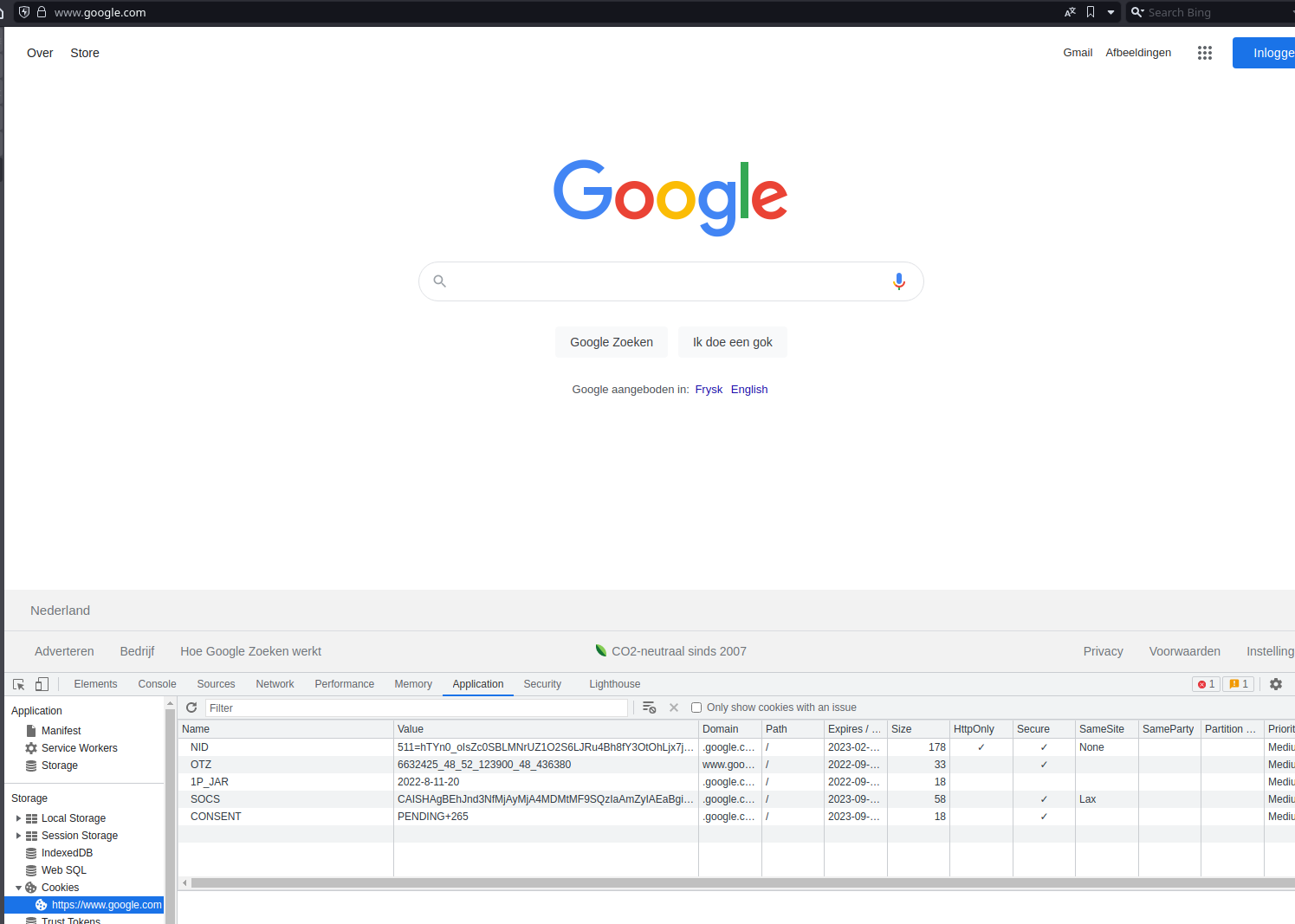
Fosstodon still remembers me.
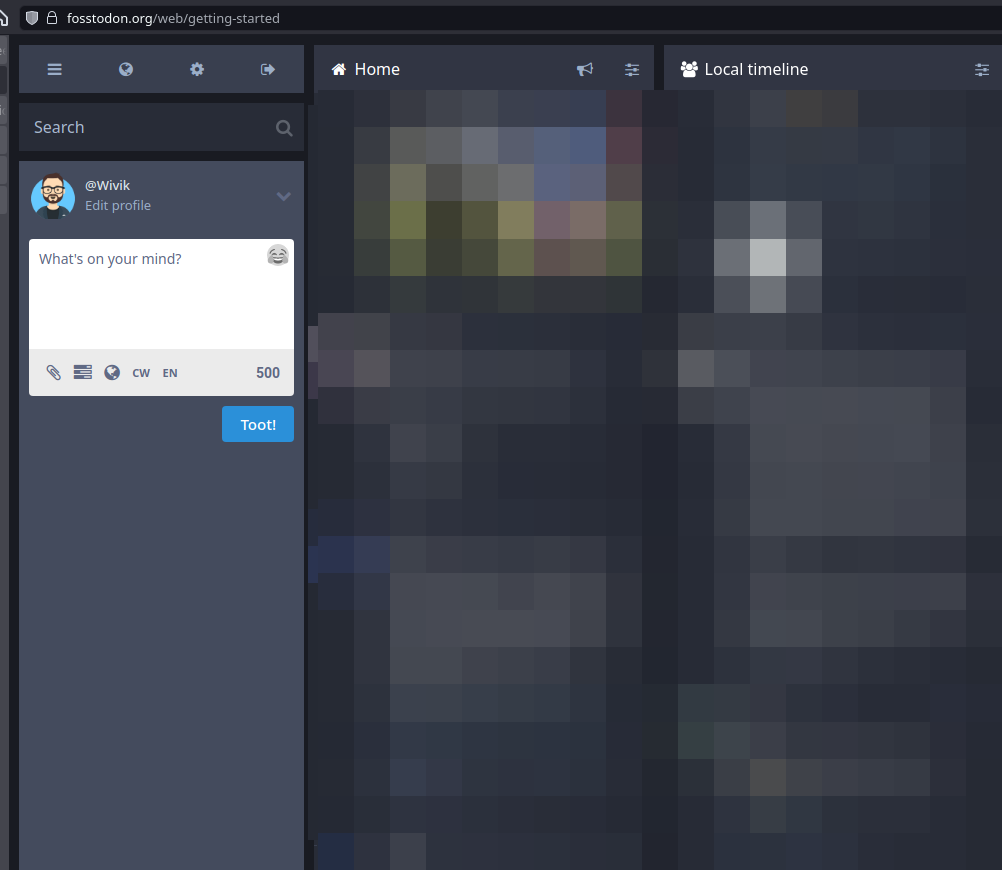
My IP changed but I’m still unprotected. What’s the purpose of these services if subscribing to one makes me still “unprotected” ? Or is it just a FUD banner ?
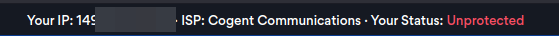
And Cover your Tracks displays the same result.
First conclusions
For a service that is supposed to offer me :
- Online privacy protection
- Security
- Anonymous surfing
- Hiding my IP
… I’ve just had my IP that changed. My browser is still full of tracking cookies, and the VPN didn’t changed anything because that’s not its purpose. If my privacy was protected, no website should had remembered me while mounting a VPN. Same if I was supposed to be “anonymous”. And I don’t feel more secure as there is no specific additional threat protection mechanism embedded into a VPN. And the “unprotected” banners confirm they’re just here to frighten the user and mean absolutely nothing. Fear is always a good commercial strategy, so I understand their purpose.
Let’s add a last item : I’ve opened an online French Newspaper filled with trackers after you accept them. You’ll see the third-party cookies in action.
Look at this cookie deposed by Google.
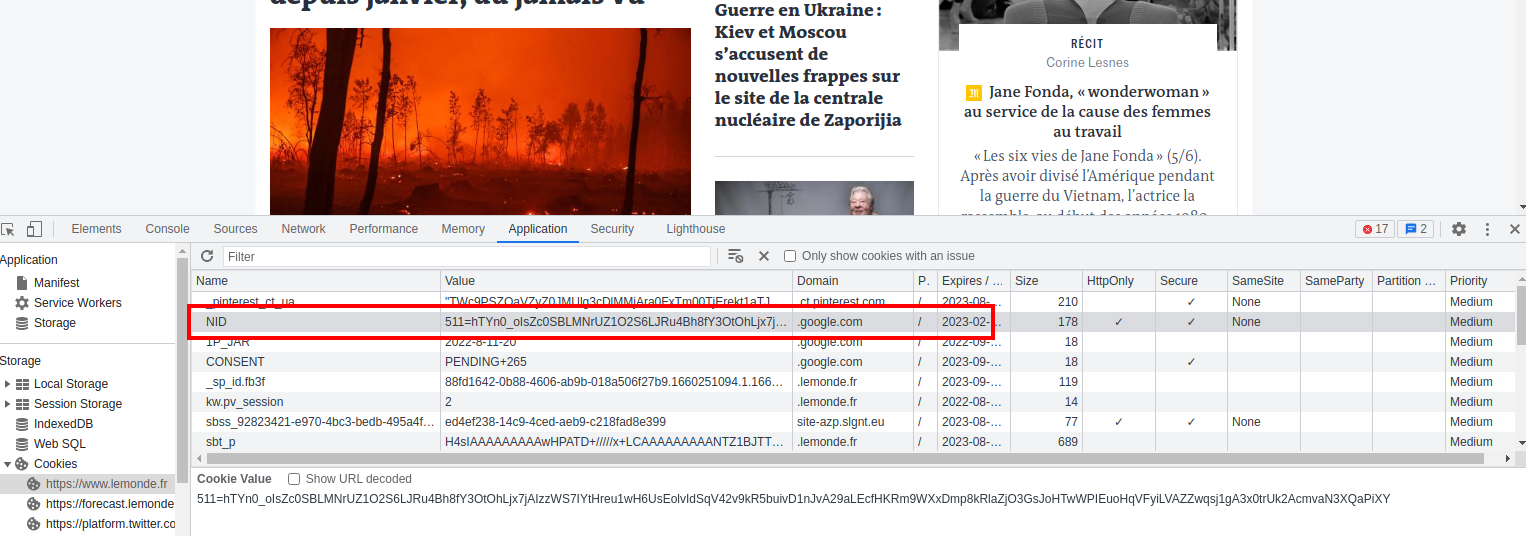

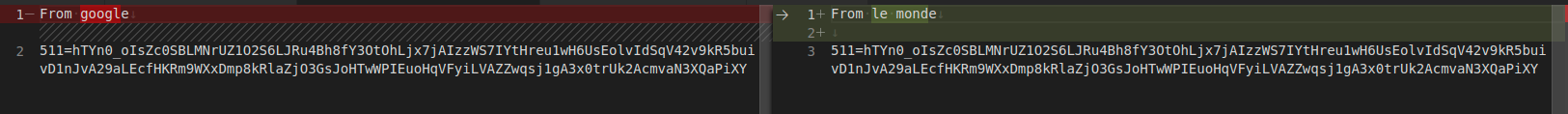
This cookie contains a data that Google can read, wherever you are, if their scripts are called by the website publisher. According to Google, it’s for storing your preferences across Google’s services.
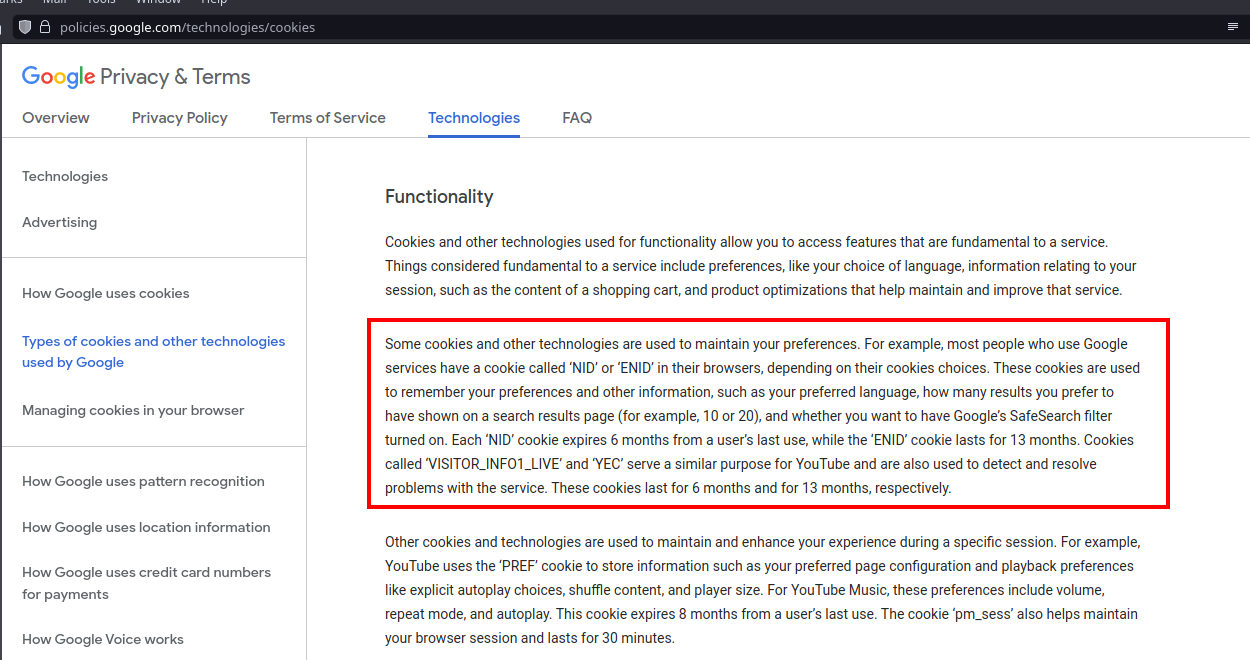
So no, a VPN doesn’t not protect your privacy because that’s your browser which is used to violate it, not your IP.
Obscure companies or jurisdiction issues
Another point in this concern is : who is the company behind the VPN service ? Are they clearly disclosed ? Is the company address an actual thing or just a letterbox ?
While visiting the five providers I’ve selected, I’ve made the following result :
- 3/5 are showing an actual office address
- The office address is displayed in the footer for 2 or them, for the 3rd one I had to search deeper
- 4/5 are disclosing the key people behind the service
- Two of them are installed in Caribbean tax-haven countries or Panama
- I’ve not been able to determine the nationality of the last one by only looking on the website
Concerning the jurisdiction issue, there are two important topics : the country where the service is installed, and the country where it is operated from.
If the service is operated from a country member of the Fives Eyes and Fourteen Eyes countries, that means the “no log” argument is really fragile because these countries are collaborating in surveillance and intelligence and have laws regarding the ISP logging activity retention and access. Some VPN services are operated by companies that looks like outside the “Five Eyes”, but actually they’re US companies with a letterbox in another country.
That’s basically what I would call a honeypot.
Fragile arguments
If I recall the arguments exposed by the commercial VPN services, a lot of them are quite fragile.
As we saw above, the “privacy”, “anonymous surfing”, “security”, and “no user tracking” features cannot be served by a VPN because the attack is mostly on the web browser. It could be prevented if the service contains an URL filter feature, at the condition of not having undisclosed whitelists for partners announcers. To be honest, I don’t know at which level the user can master this part of the service. “Hiding your IP” would be the only benefit of a VPN, but as the IP is not a discriminating data, it’s only interest would be to access geo-blocked content or bypassing a Government Internet censorship (which could be an illegal activity in these kind of countries).
They also all expose the “independently audited” and “no log” arguments. But that’s just promises, it’s basically impossible to verify it unless you can actually audit the infrastructure behind the service. Moreover, if you use a free service, you can be assured that your data will be collected, analyzed and sold to make profit. That’s the most usual economic model for online free services. Regarding the “independently audited” argument, I haven’t found any of these studies reports displayed on the websites, maybe I haven’t searched enough. Only one displayed the link to the studies. For companies selling trust and privacy, I would naively think they would easily expose these “independent audits”.
The privacy policy is also selling a really trusty service, but that’s just words, not actions. Trust cannot be gained just because they paid Youtubers to say so.
Also, the traffic inside the VPN may be encrypted by the client, but are you sure there is no man-in-the-middle decrypting the traffic on the fly ? That’s basically what the companies proxies can do thanks to a root certificate installed on their employees computers.
On the five I’ve compared, only one has published its various clients as open-source releases. The transparency of the provider and verifiable proofs should be mandatory for anybody who wants to subscribe these services. Or it would just be a leap of faith.
How can I be actually privacy safe on the Internet ?
First, you may have noticed I haven’t written “anonymous”, because I don’t believe in this possibility on the Internet. There is always a trace that will betray your supposed anonymity. Cross data analysis is the specialty of numerous big tech companies, so don’t be too confident about your “anonymity”.
If you want to protect yourself from the device fingerprinting, you’ll need at least to use content blockers (like uBlock Origin or the one in your browser if it’s trusty enough). You may need to disable at least the third-party cookies, but I recommend also to clear all of them at the end of your session with the local storage and session data. As Vivaldi does not have an advanced cookie manager (sadly), I’m using the extension Cookie Auto-Delete. With a whitelist for website I know I can trust, and the other sees their local content automatically suppressed after the last tab is closed.
I also recommend using the extension Privacy Redirect which will redirect your surfing to alternative front-ends of famous websites known for their violation of privacy (like Youtube, Twitter, etc). For example, on Youtube you’ll be redirected to an Invidious instance, for Twitter a Nitter one, etc. You can enable which one you want. That’s pretty convenient as most of the links today are to Youtube of social medias. Also, avoid clicking on reduced URLs, they integrate tracking and ads. Some extensions can resolve them to the actual URL. On my side, I usually open these link in private browsing. Always check the link URL before clicking on it, you may avoid some nasty surprises.
Disabling Javascript is pretty effective against tracking, but the user experience may be strongly degraded.
Using the Incognito/Private browsing mode, but remember that Google Chrome Private browsing does not protect from tracking. BTW, you should obviously avoid Google Chrome. A Chromium-based browser could remain safer, especially the privacy-oriented like Vivaldi or Brave because their integration is made to disable the tracking features that Google injects into Chromium. I’m not confident about Brave however, because they had some shady history regarding their practices like injecting into URLs some affiliate ID (that’s not the case anymore) and I don’t like their economic model which replace the Ads by their own one. If your not confident enough about these one, you may use Tor Browser which is based on Firefox and enforced for privacy. Tor Browser disables the OpenGL Canvas and other features used for fingerprinting a browser.
Regarding fingerprinting prevention, I’ve observed two strategies. On could be to generate a random fingerprint, but the trackers may still be able to cross the browsing activities and merge the various identifiers into one. Another one would be to appear the most generic possible so the tracking system cannot discriminate your activity from the other one, making your activity more generic.
The browsers also have settings to enforce privacy. For example, Vivaldi has a setting that automatically remove the tracking information in URL used to know if came from a link in a email, a partner, etc.
And in the most desperate case, the usage of the Tor Network is recommended. I’ve never used it, so I can’t really tell about.
Disable the Advertising ID in your OS (available for Microsoft Windows, Apple Systems and Android).
For Mobile devices, ensure you don’t give too much permissions to your applications. Always put in question what they ask (ex : why a compass would ask to read your contacts ?) and refuse what seems to be shady. If the application doesn’t work because of these missing permissions, delete it, that’s a crap.
Avoid “VPN” and other similar application on Google Play without inquiring first about them, most of them are filled with spywares and malwares ! Install Exodus Privacy to check the amount of trackers you have installed.
However, all of these recommendations can have impacts over the user experience. Some services may be broken and you may encounter irritating bugs and behaviors. But sadly, there are no magic ways, and a VPN Service itself cannot protect yourself from all of the tracking made on the Internet. I still hope this article would have been useful to privacy concerned people. If you have other tips or feedback to share, don’t hesitate !
